Cyphon For Mac

Apr 17, 2015 How to DDoS using Hulk.py on Mac OS X Chip-Hacker. Cyphon for Mac OS - DDoS Software. Honorbuy Mobile Shop Recommended for you. PCSX2 Emulator for Mac.
Record video in realtime from any Syphon-enabled application, and capture stills.
Ahead of Formatting: What do you plan to use your WD My Passport Drive For?Pause a few minutes. A place to save your documents?. Using the My Passport drive as your Time Machine backup disk?. Before you go aheadand format your shiny new drive, think about your planned use.For example are you thinking of:. 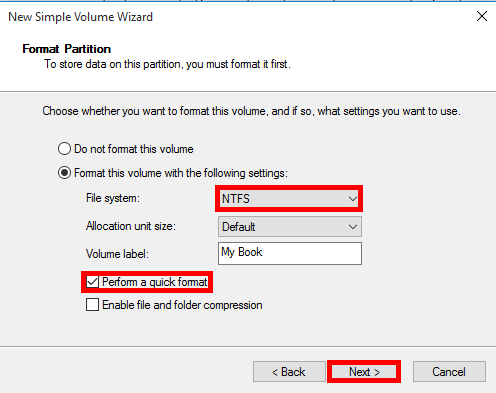 Do you plan to share files with Mac and a Windows PC?Then you’ll need your My Passport drive in the right format.I have a document for you.
Do you plan to share files with Mac and a Windows PC?Then you’ll need your My Passport drive in the right format.I have a document for you.
Download
Download Syphon Recorder (version 18)
The previous version, 15, is available here. It does not support macOS Catalina.
About
Syphon Recorder 18 was made possible by a lot of hard work from David and Ray at Vidvox.
Syphon Recorder was originally written by Tom Butterworth and Anton Marini. Syphon Recorder is free, with no restrictions on its use. For support please check the Help menu in the app, then visit the Syphon forum.
Changes
18
- Add support for macOS Catalina.
- Add support for H.264 video.
- Add support for Apple Lossless audio.
- Remove support for the Sheer codecs.
15
- Fix an issue which could cause checks for new versions to fail.
14
- Fix reliability issues affecting MacOS 10.11 El Capitan.
Beta 13
- Add support for recording mono audio from mono devices.
- Add support for recording more than two audio channels when devices support it.
- Fix issues recording AAC from some audio hardware.
Beta 12
- Fix an issue which caused low frame-rates on MacOS Mavericks if the app was off-screen.
Beta 11
- Fix an issue which caused corrupted sound to be recorded from some third-party hardware.
- Fix an issue which caused unexpected behaviour when using some third-party audio hardware.
Beta 10
- If a recording is unexpectedly ended an attempt will be made to recover it when recovery becomes possible.
- Remove support for the Motion JPEG B codec. If you were previously using this codec, Photo-JPEG will be selected instead.
- Fix an issue which caused some recordings to exhibit a color-shift when viewed in some applications.
- Fix an issue which caused unexpected file names to be used occasionally.
- Add support for Retina displays.
Beta 9
- Fix an issue which caused a slight color-shift in recordings.
- Add support for the Photo-JPEG codec.
- Improve image quality when recorded dimensions exactly match the source.
Beta 8
- Add support for recording AAC audio.
- Improve audio/video synchronization.
- Fix an issue with handling some unusual Syphon servers.
Beta 7
- Fix a crash which could occur if you recorded a still image as a movie with an audio track. Thanks to Adam Fenn for reporting this.
- Fix a memory leak.
Beta 6
- Bug fixes
- Interface tweaks
Beta 5
- Append date and time to saved recordings and snapshots
- Fix a problem which arose if you took a lot of snapshots in quick succession
Beta 4
- Add support for Apple ProRes 4444 codec (requires Final Cut Studio be installed)
- Add support for Sheer codecs (www.bitjazz.com/sheervideo/)
- Add preference to ignore the alpha channel for codecs which support it
- Improve performance and reliability
Beta 3
- Changes to avoid a bug in MacOS X 10.6.7 which prevented sound ever being recorded.
Beta 2
- Add support for Apple ProRes 422 codecs (requires Final Cut Studio be installed)
- Fix issue where movies were unplayable if the app quit while recording
- Create a playable movie even if a disk becomes full while recording
- Improve recovery and reporting associated with other less common errors
Beta 1
- Initial Public Beta
| Original author(s) | RSnake |
|---|---|
| Initial release | 17 June 2009 |
| Stable release | 0.7 |
| Written in | Perl |
| Platform | Cross-platform |
| Size | 36 kb |
| Type | Hacking tool |
| Website | ha.ckers.org/slowloris/ |
Slowloris is a type of denial of service attack tool invented by Robert 'RSnake' Hansen which allows a single machine to take down another machine's web server with minimal bandwidth and side effects on unrelated services and ports.
Slowloris tries to keep many connections to the target web server open and hold them open as long as possible. It accomplishes this by opening connections to the target web server and sending a partial request. Periodically, it will send subsequent HTTP headers, adding to—but never completing—the request. Affected servers will keep these connections open, filling their maximum concurrent connection pool, eventually denying additional connection attempts from clients.[1]
Affected web servers[edit]
This includes but is not necessarily limited to the following, per the attack's author:[1]
- Apache 1.x and 2.x
- dhttpd
- Websense 'block pages' (unconfirmed)
- Trapeze Wireless Web Portal (unconfirmed)
- Verizon's MI424-WR FIOS Cable modem (unconfirmed)
- Verizon's Motorola Set-top box (port 8082 and requires auth - unconfirmed)
- BeeWare WAF (unconfirmed)
- Deny All WAF (patched) [2]
- Flask (development server)
Because Slowloris exploits problems handling thousands of connections, the attack has less of an effect on servers that handle large numbers of connections well. Proxying servers and caching accelerators such as Varnish, nginx, and Squid have been recommended[3] to mitigate this particular kind of attack. In addition, certain servers are more resilient to the attack by way of their design, including Hiawatha,[4]IIS, lighttpd, Cherokee, and CiscoCSS.
Mitigating the Slowloris attack[edit]
While there are no reliable configurations of the affected web servers that will prevent the Slowloris attack, there are ways to mitigate or reduce the impact of such an attack. In general, these involve increasing the maximum number of clients the server will allow, limiting the number of connections a single IP address is allowed to make, imposing restrictions on the minimum transfer speed a connection is allowed to have, and restricting the length of time a client is allowed to stay connected.
In the Apache web server, a number of modules can be used to limit the damage caused by the Slowloris attack; the Apache modules mod_limitipconn, mod_qos, mod_evasive, mod security, mod_noloris, and mod_antiloris have all been suggested as means of reducing the likelihood of a successful Slowloris attack.[1][5] Since Apache 2.2.15, Apache ships the module mod_reqtimeout as the official solution supported by the developers.[6]
Other mitigating techniques involve setting up reverse proxies, firewalls, load balancers or content switches.[7] Administrators could also change the affected web server to software that is unaffected by this form of attack. For example, lighttpd and nginx do not succumb to this specific attack.[1]
Notable usage[edit]
During the protests that erupted in the wake of the 2009 Iranian presidential election, Slowloris arose as a prominent tool used to leverage DoS attacks against sites run by the Iranian government.[8] The belief was that flooding DDoS attacks would affect internet access for the government and protesters equally, due to the significant bandwidth they can consume. The Slowloris attack was chosen instead, because of its high impact and relatively low bandwidth.[9] A number of government run sites were targeted during these attacks, including gerdab.ir, leader.ir, and president.ir .[10]
A variant of this attack was used by spam network River City Media to force Gmail servers to send thousands of messages in bulk, by opening thousands of connections to the Gmail API with message sending requests, then completing them all at once.[11]
Similar software[edit]
Since its release, a number of programs have appeared that mimic the function of Slowloris while providing additional functionality, or running in different environments:[12]
- PyLoris – A protocol-agnostic Python implementation supporting Tor and SOCKS proxies.[13]
- Slowloris – A Python 3 implementation of Slowloris with SOCKS proxy support.[14]
- Goloris – Slowloris for nginx, written in Go.[15]
- QSlowloris – An executable form of Slowloris designed to run on Windows, featuring a Qtfront end.[16]
- An unnamed PHP version which can be run from a HTTP server.[17]
- SlowHTTPTest – A highly configurable slow attacks simulator, written in C++.[18][19]
- SlowlorisChecker – A Slowloris and Slow POST POC (Proof of concept). Written in Ruby.[20]
- Cyphon - Slowloris for Mac OS X, written in Objective-C.[21]
- sloww - Slowloris implementation written in Node.js.[22]
- dotloris - Slowloris written in .NET Core [23]
See also[edit]
References[edit]
- ^ abcd'Slowloris HTTP DoS'. Archived from the original on 26 April 2015. Retrieved 26 June 2009.CS1 maint: BOT: original-url status unknown (link)
- ^'Archived copy'(PDF). Archived from the original(PDF) on 1 February 2014. Retrieved 15 May 2013.CS1 maint: archived copy as title (link)
- ^'How to best defend against a 'slowloris' DOS attack against an Apache web server?'. serverfault.com. Retrieved 28 December 2016.
- ^'Performance testing while under attack'. hiawatha-webserver.org. 28 February 2014.
- ^'mod_noloris: defending against DoS'. niq's soapbox. Retrieved 7 January 2012.
- ^'mod_reqtimeout - Apache HTTP Server'. Httpd.apache.org. Retrieved 3 July 2013.
- ^Breedijk, Frank (22 June 2009). 'Slowloris and Nkiller2 vs. the Cisco CSS load balancer'. Cupfighter.net. Retrieved 7 January 2012.
- ^Zdrnja, Bojan (23 June 2009). 'ISC Diary Slowloris and Iranian DDoS attacks'. Isc.sans.org. Retrieved 7 January 2012.
- ^[1]Archived 29 June 2009 at the Wayback Machine
- ^[2]Archived 11 August 2009 at the Wayback Machine
- ^Vickery, Chris (6 March 2017). 'Spammergate: The Fall of an Empire'. MacKeeper Security Watch. Archived from the original on 6 March 2017.
- ^Robert “RSnake” Hansen. 'Slowloris'(PDF). SecTheory. Retrieved 7 January 2012.
- ^'PyLoris'. MotomaSTYLE. 19 June 2009. Archived from the original on 15 July 2009. Retrieved 7 January 2012.
- ^'Slowloris rewrite in Python'. Retrieved 10 May 2017.
- ^valyala. 'Slowloris for nginx DoS'. Retrieved 4 February 2014.
- ^'How to help take down gerdab.ir in 5 easy steps'. cyberwar4iran. 28 June 2009. Retrieved 7 January 2012.
- ^'Full Disclosure: apache and squid dos'. Seclists.org. 19 June 2009. Retrieved 7 January 2012.
- ^'Testing Web Servers for Slow HTTP Attacks'. qualys.com. 19 September 2011. Retrieved 13 January 2012.
- ^'shekyan/slowhttptest: Application Layer DoS attack simulator'. GitHub. Retrieved 19 April 2017.
- ^'Simple script to check if some server could be affected by Slowloris attack'. github.com/felmoltor. 31 December 2012. Retrieved 31 December 2012.
- ^abilash. 'Slowloris for OSX'. Retrieved 8 April 2017.
- ^Davis, Ethan (17 February 2018), sloww: Lightweight Slowloris attack CLI in Node, retrieved 18 February 2018
- ^Bassel Shmali. 'Slowloris written in .Net core'.
External links[edit]
- Apache attacked by a 'slow loris' article on LWN.net
